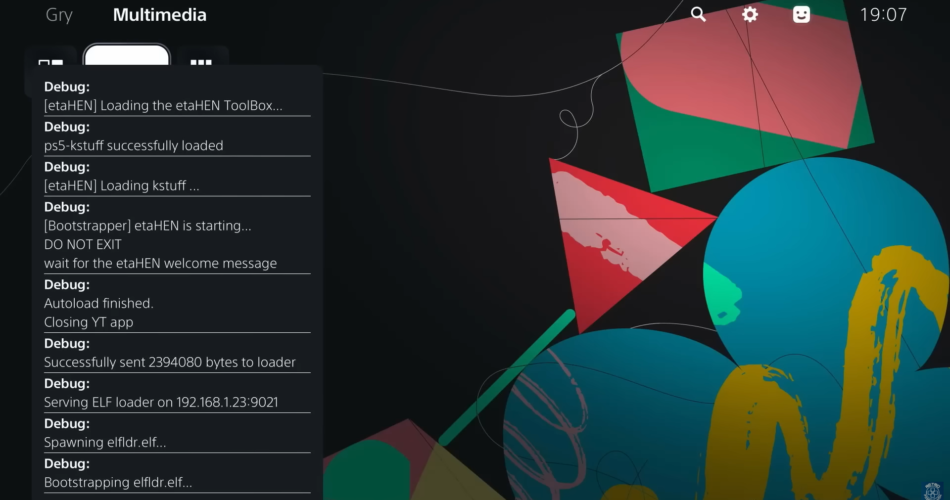
Y2JB, the proof-of-concept exploit that exploits the official YouTube app for the PlayStation 5 console, continues to progress. Well-known developer Gezine has posted an image on X that documents a significant advancement in its work: according to the author, the launch has been successful.
No instability, the task achieved 100% success, the post states, while reliability and repeated execution tests have now produced stable and reproducible results.
This level of stability is often a necessary step before tackling the more complex and delicate technical phases of the exploit development process.
In the information shared, Gezine explains that, after having managed to obtain the ability to arbitrarily read and write memory, the next step will be the construction of a ROP chain.
The developer warns that making a complete ROP will take longer: the technique, by its nature, is meticulous and requires identifying and combining existing code fragments in memory in a precise and compatible way.
This is why, despite the tangible progress achieved so far, the road to a practical and distributed solution remains long.
For those who aren’t aware, ROP (Return-Oriented Programming) allows you to control the behavior of a program by reusing short sequences of instructions already present in memory, the so-called gadgets, thus avoiding the injection of new executable code.
This approach is particularly relevant in secure environments where arbitrary code execution is prevented by modern security measures.
Finding and assembling useful gadgets takes time , testing, and patience, explaining Gezine ‘s warning about the need to work methodically.
The community reaction was immediate and lively: many users interpreted the post as part of the PlayStation 5 jailbreak effort, with discussions about the difficulty of bypassing checks like ASLR and references to specific firmware versions that might be affected.
From a technical perspective, observers and experts point to areas that have given rise to vulnerabilities in the past, such as browser rendering engines or parts of the kernel, but at the same time emphasize that there is still a lot of work to be done between demonstrating a working concept and releasing a reliable and secure tool.
Source: x.com, biteyourconsole.net

Comments