The PlayStation 5 homebrew scene continues to evolve, and with it the tools that make it possible. One of the most practical and versatile projects is undoubtedly the ESP8266/ESP32 PlayStation 5 Web Exploit Server, which in its latest release, v1.50, introduces significant updates and stability improvements.
If you own a PS5 with firmware between 1.00 and 5.50 and an ESP microcontroller (such as a NodeMCU or a Wemos D1), you have the key to unlocking your console’s homebrew potential, all offline after an initial setup.
What is the PlayStation 5 Web Exploit Server?
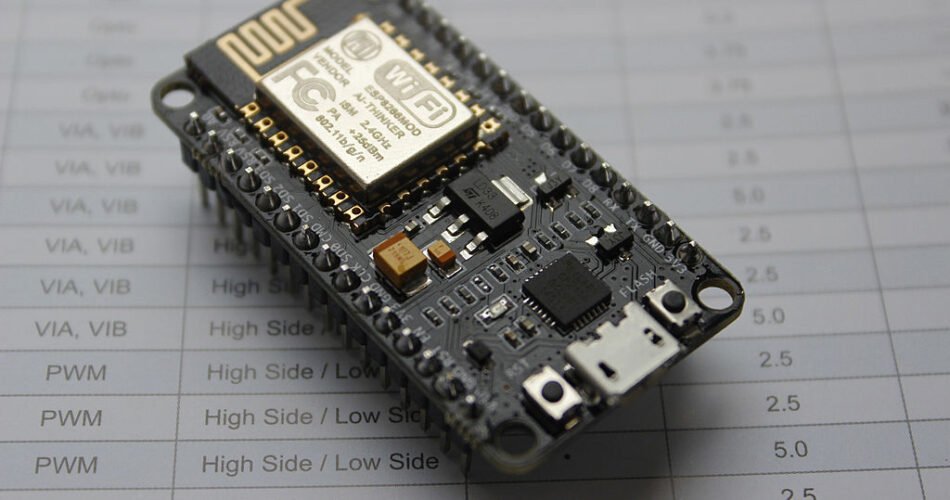
Simply put, it’s a lightweight web server running on an ESP8266 or ESP32 board. This board creates a WiFi network to which you connect your PS5, serving the web page containing the “UMTX2” jailbreak exploit directly to the console. The main advantage? After the first visit and the exploit cache, you can jailbreak completely offline in the future, without needing to reconnect to the internet.
What’s New in Version 1.50
The latest release, v1.50, is not just a maintenance release but brings significant updates to key components:
kstuffUpdated to v1.6.4: Kernel exploit is more stable and reliable.kstuff-toggleUpdated to v0.3: Improvements in kernel feature handling.ftpsrvUpdated to v0.13: The built-in FTP server, essential for transferring files to and from the PS5, has been improved.- Improved data compression: A behind-the-scenes change that frees up valuable storage space on the ESP memory, allowing for new payloads and features to be added in future updates.
The author, Vladimir Cucu, confirms that it works on the ESP32 and ESP32-S3, while other variants have not been tested.
Available Payloads
Once the server is started, you will have access to a number of essential payloads:
- etaHEN: The reference homebrew environment for PS5, required for running homebrew apps and games.
- byepervisor & elfldr: Support payload for loading executable files.
- kstuff & kstuff-toggle: The core of the kernel exploit and its management tool.
- ftpsrv: An FTP server to manage files on your PS5.
- webkit-cache-remover: A useful tool for clearing your browser cache if you encounter problems.
Quick Installation and Use Guide
Getting your own server up and running is a simple process.
What you need:
- An ESP8266 or ESP32 board (a NodeMCU will do just fine).
- The precompiled binary of v1.50 (downloadable from the project’s GitHub release page).
- A software to flash the firmware, such as NodeMCU PyFlasher (for Windows and macOS) or esptool (cross-platform).
Procedure:
- Flashing the Firmware: Download the file
esp-ps5-exploit-server-v1.50.binand upload it to your ESP board using your chosen flashing tool. - WiFi Connection: Turn on your ESP. Among the available WiFi networks, you should see a new network called
PS5_WEB_AP. Connect your PlayStation 5 to this network. The password ispassword. - Running the Exploit: On your PS5, open your browser and go to “ESP Host FPKG.” This will take you to the exploit page. Follow the on-screen instructions to jailbreak. Important: This first time, the page will be cached on your PS5.
- Offline Use: From now on, you no longer need to connect your PS5 to the ESP’s WiFi network to jailbreak. Simply open the PS5 User Guide (if you used a specific fork) or the “ESP Host FPKG” option from your browser cache, even without an internet connection!
Important Note: If you would like the exploit to be accessible directly from the PS5 User Guide (a cleaner method), we recommend checking out the PS5-Server fork, which 0x1iii1iiimplements this functionality.
Credits
A huge thank you goes to the community and developers who make this possible. This project is inspired by the work of:
- stooged for the original PS5-Server project.
- frwololo for the PS4_PS5-ESP8266-Server project.
Soruce: github.com

Comments